If you have to test a JAR file for log4shell vulnerability but do not want to install any tools / do not trust them, a possible no-install low-ceremony is to use Grype in its Docker mode, which allows you to install absolutely nothing on your machine.
Only prerequisite is to have Docker installed on your machine and, of course, the JAR file or folder you want to test.
First, create a Dockerfile like this :
FROM scratch
ADD test.jar .
Or in the case of a complete folder to test :
FROM scratch
ADD folder-under-test/ .
Now compile the Docker image using a similar command :
docker run –t jpgouigoux/testjar .
You will of course adjust to your Docker account so you can upload the image to the public registry (unless of course your JAR files are confidential, and in this case you need to operate on a private registry).
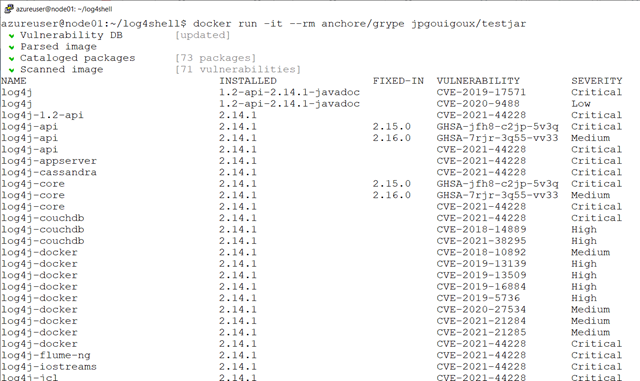
It is then easy to use Grype to assess the vulnerability of you SUT, with the following command that will leave your local machine exactly as it was before, only displaying the report :
docker run –rm anchore/grype jpgouigoux/testjar
The results (in this case, showing the CVS 2021-4428 vulnerability) will quickly be displayed in text :